In today’s digital-first era, modern organizations face a rapidly evolving landscape of cyber threats that demand proactive and comprehensive security strategies. Cybercrime has shifted from sporadic attacks to persistent campaigns targeting organizations of every size, exploiting gaps in outdated network defenses. Amid this backdrop, network segmentation stands out as a particularly powerful method for strengthening the security of Wide Area Networks (WANs). Effective segmentation strategies not only defend against lateral movement of threats but also optimize network performance, simplify the management of distributed environments, and ensure regulatory compliance across diverse technological landscapes. These layers of protection are made increasingly efficient and adaptive with advanced SD-WAN solutions, which enable organizations to respond to evolving threats without introducing unnecessary complexity to their IT operations.
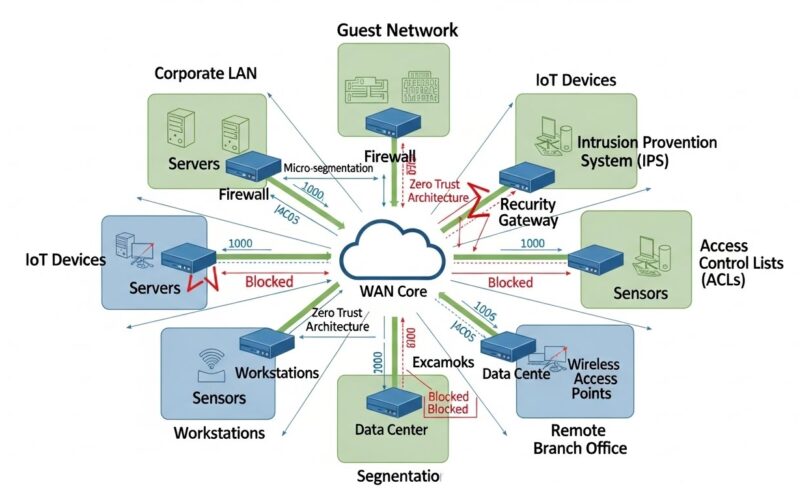
Network segmentation involves dividing a single network architecture into smaller, isolated subnetworks, often referred to as segments or zones, each governed by granular security policies tailored to the unique risk profile of that segment. This approach dramatically reduces the exposure of critical assets, making it significantly more difficult for cyberattackers to traverse the network even if they gain a foothold. As organizations’ digital footprints expand with the adoption of remote work technologies, increasing reliance on cloud platforms, and the proliferation of IoT devices, the necessity of such segregation becomes apparent. Segmentation emerges as both an operationally practical and strategically essential requirement for maintaining resilient defenses and business continuity.
Understanding Network Segmentation
Network segmentation is the foundational process of dividing a broad computer network into several smaller subnetworks, or “segments.” This practice utilizes tools and technologies such as VLANs, firewalls, and software-defined networking to implement granular access controls and restrict communication pathways between devices and applications. Segmentation can take multiple forms; for example, it may involve isolating payment processing systems from general corporate networks or dedicating separate network paths for development and production environments. By segmenting systems that handle critical business operations and storing sensitive data, organizations establish robust security barriers that confine potential breaches, reduce broadcast traffic, and limit damage to the affected segment.
By strictly limiting communications between segments, companies lower the risk of a single compromised endpoint escalating into a widespread network breach. Attackers unable to move from one segment to another find their options greatly restricted, increasing the likelihood of prompt detection and containment. This model also prevents unnecessary data exposure across business units, which is crucial for achieving regulatory compliance and maintaining trust with customers, partners, and regulatory agencies. Ultimately, segmentation organizes internal traffic flow so that disruptions in one area do not negatively impact the security or performance of unrelated segments.
Benefits of Network Segmentation
- Reduced Congestion: Isolating groups of devices and applications minimizes broadcast domains and reduces unnecessary data traffic, relieving congestion and ensuring more responsive connectivity within each segment. This compartmentalization leads to shorter response times for applications and devices that share the same segment.
- Enhanced Security: Clearly defined segments significantly increase the challenge for cybercriminals to gain access to sensitive areas of the network. By creating fortified boundaries, segmentation contains potential threats and limits east-west movement, meaning that even if an initial compromise occurs, attackers face formidable obstacles when attempting to move towards high-value targets, such as databases or intellectual property repositories.
- Improved Performance: Segmentation enables performance-sensitive applications and mission-critical operations to operate without being hindered by less critical or bandwidth-intensive services. By preventing competition for network resources between unrelated business functions, organizations achieve more predictable and stable network performance, which is essential for transaction processing, VoIP, and time-sensitive applications.
Challenges in Implementing Network Segmentation
Effective network segmentation requires more than just technical know-how—it demands a strategic understanding of the organization’s assets, business-critical workflows, and regulatory obligations. Common challenges encountered in the implementation of segmentation initiatives include:
- Complexity: Modern enterprise networks can contain thousands—even tens of thousands—of endpoints, with numerous interdependent applications and processes. This complexity makes the design, deployment, and ongoing maintenance of segmentation zones a highly challenging and resource-intensive process.
- Asset Inventory Limitations: The success of any segmentation project depends on maintaining a comprehensive and up-to-date inventory of network assets. Overlooking even a single device, application, or data flow can undermine the integrity of the entire segmentation initiative, creating hidden pathways that attackers could exploit.
- Legacy Infrastructure: Many established organizations operate on infrastructure that predates modern segmentation techniques. These legacy systems often lack native support for advanced segmentation and granular access control, requiring substantial investments in hardware, software upgrades, or retraining personnel before full benefits can be realized.
Role of SD-WAN in Network Segmentation
The advent of SD-WAN has fundamentally transformed the way organizations approach segmentation across wide-area networks. Whereas traditional WAN architectures often lacked the flexibility, visibility, and centralized control necessary for dynamic, policy-driven segmentation, SD-WAN introduces a unified management layer that empowers IT teams to orchestrate and enforce segmentation policies from a single interface. This advancement provides enhanced control over remote sites and cloud resources while reducing operational overhead.
With SD-WAN, organizations can more easily implement micro-segmentation—a practice that divides networks into highly specific, secure zones based on business requirements or risk levels. Micro-segmentation enables organizations to tightly align security boundaries with business objectives, such as separating transactional systems from guest Wi-Fi networks or isolating critical workloads in public or private clouds. Automated traffic classification, real-time analytics, and streamlined policy updates offered by SD-WAN solutions further enable organizations to adapt to shifting needs with minimal manual involvement. According to reports from Network World, companies deploying SD-WAN platforms achieve significant gains in agility and consistency when implementing complex segmentation strategies across their distributed enterprise environments.
Implementing Effective Network Segmentation
- Conduct a Thorough Network Assessment: Start by identifying every networked asset, system, and device, along with conducting a comprehensive audit of all data flows, access points, and related risks. Robust discovery and mapping are vital in identifying dependencies and determining where segmentation zones will provide the greatest security impact.
- Define Segmentation Policies: Establish clear, detailed policies that specify allowed communications, user and device access rights, and permitted inter-segment traffic flows. These policies should be closely aligned with organizational roles, compliance mandates (such as PCI DSS or HIPAA), and operational priorities to ensure they are both enforceable and relevant to business objectives.
- Utilize Advanced Technologies: Deploy cutting-edge SD-WAN platforms, next-generation firewalls, and network access control solutions. Leveraging these technologies ensures enforcement of segmentation policies at the network edge and core, provides deep visibility for monitoring, and enables automated, timely responses to suspicious activity.
- Regularly Review and Update Segmentation Strategies: Cyber threats, business models, and technologies continue to evolve. Regular assessment, ongoing validation, and continuous adjustment of segmentation strategies ensure defenses remain effective and that network architecture adapts to new threats, regulatory demands, and business expansions.
Final Thoughts
As cyber threats continue to increase in sophistication and frequency, effective segmentation stands as a foundational pillar in securing modern WANs. By leveraging dynamic SD-WAN architectures, maintaining up-to-date inventories of assets, and instituting a cycle of continuous policy review, organizations can maximize both their defenses and operational flexibility. Organizations that adopt best practices and draw on insights from trusted external resources put themselves in the strongest position, not only to withstand today’s security challenges but also to remain resilient as tomorrow’s threats emerge. In an era where network perimeters have largely disappeared, segmentation ensures that every segment of your organization’s network is prepared to counter sophisticated intrusions while enabling uninterrupted business operations.